Using ModSecurity on your VPS
ModSecurity is an web application firewall that runs in conjunction with your web server. It’s designed to protect your web sites from a ra nge of malicious attacks and provides various features including HTTP traffic monitoring, logging and real-time analysis.
nge of malicious attacks and provides various features including HTTP traffic monitoring, logging and real-time analysis.
ModSecurity rules are based on a series of regular expressions. Each rule is designed to block commonly known exploits that are found in most popular content management systems, shopping carts and other web applications.
When software developers create a web application, theme or plugin they may forget to take the usual precautions to secure their code properly. In doing so they have created an exploit or vulnerability that can be taken advantage of by a hacker.
In the majority of cases ModSecurity will block legitimate attacks by hackers however there will be times when a false positive is generated and a visitor performing a legitimate task is blocked.
Locating a ModSecurity block
If you have a visitor who is unable to access your web site then you may want to check to see if they have triggered a ModSecurity rule on your server.
The most immediate solution to this issue is to remove the mod_sec blocked IP rules in ConfigServer Security & Firewall. This will allow the IP’s of those clients that were being blocked to work again.
First you will need to locate your visitor’s IP address. Read the following support article below for a step by step guide on how to do this.
Remove a Block In ConfigServer Security & Firewall
Usually a ModSecurity rule will look something like this:
192.168.1.1 # lfd: (mod_security) mod_security (id:960006) triggered by 192.168.1.1 (AU/Australia/remoteserver.net): 5 in the last 3600 secs - Fri Oct 12 13:25:40 2015
In our example the visitor’s IP address is 192.168.1.1 and they triggered the rule with the ID of 960006.
When you have located the rule that your visitor has triggered be sure write down the ID number for future reference before removing the block.
Reviewing the ModSecurity ID
When a block is triggered against a specific rule it’s recorded at the log view via Home » Security Center » ModSecurity Tools.
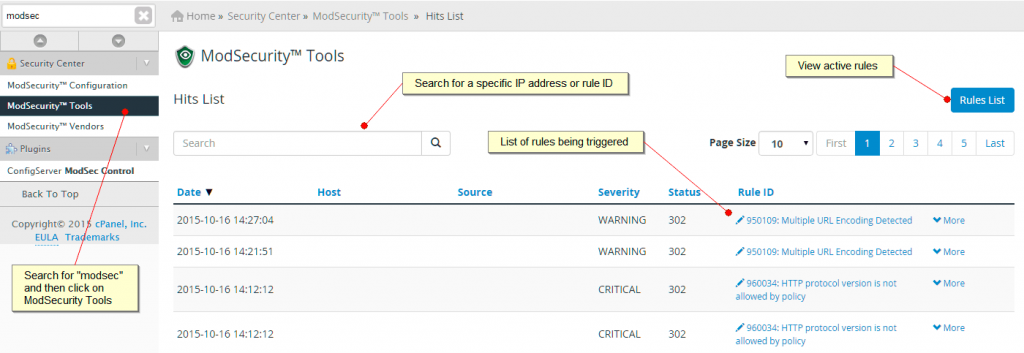
Within the ModSecurity Tools centre you can search for a specific IP address so that you can view previous blocks generated for a particular visitor.
Below the search bar is a list of all the previous rules that were triggered including the name of the web site (Host) and the corresponding IP address (Source). The Rule ID along with a short description are provided within the Rule ID column. You can click on the More button to see more specific details about the specific action that occurred when the visitor triggered the rule.
If you would like to learn more about a specific rule then click on the Rules List button.
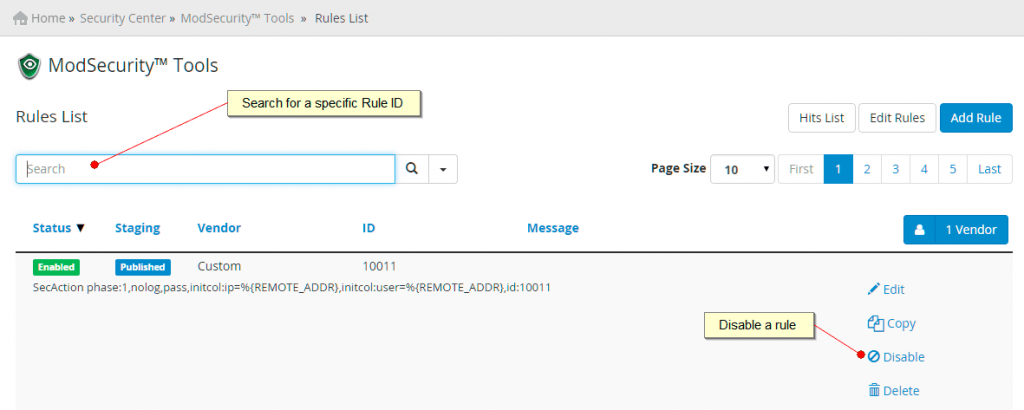
Within this screen you can edit the parameters of the rule, or disable it completely.
We would recommend that you don’t use this feature and instead only disable the rule on a per domain basis only. This will be described in the next section. Disabling the rule on a permanent basis is would prevent the rule from protecting other accounts that you might be hosting.
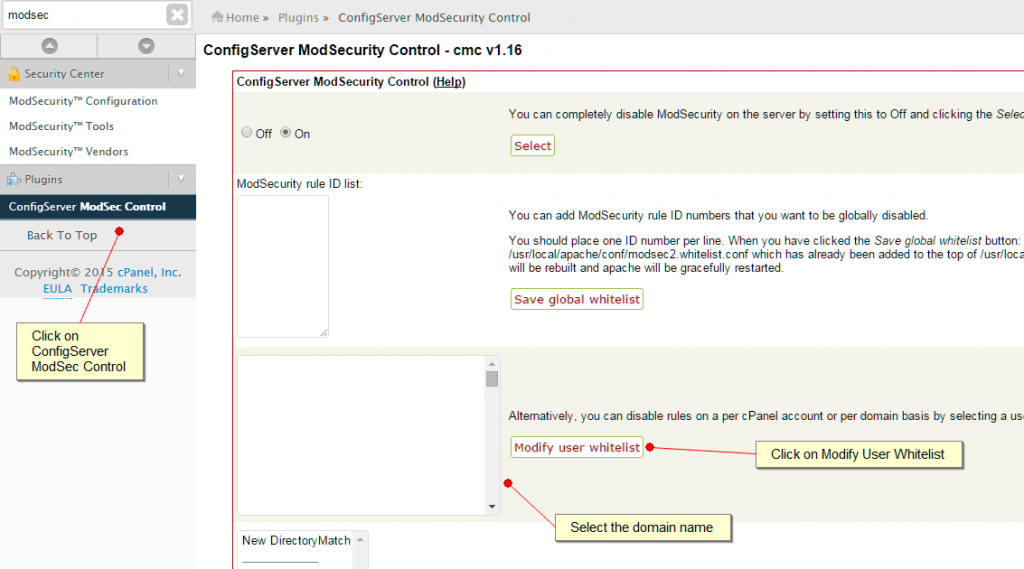
To disable the rule on a per domain basis go to ConfigServer ModSec Control and then select the domain name you wish to whitelist. Click on Modify User Whitelist. Enter the Rule ID that you previously wrote down and then save the changes. Now only this particular domain will be whitelisted from this rule.
Research the Rule ID
The best course of action is too research the rule and attempt to determine what is causing the trigger. In some instances it can be a specific browser plugin or desktop anti virus software package that is being overly aggressive in it’s attempts to connect to your client’s web site. In other cases it can be an issue with your CMS, shopping cart or other web application where specific PHP code contained in the site, a plugin or template is causing ModSecurity to generate a block.
Though there are many things that can trigger ModSecurity when working on or accessing your site, the first things you should check are the following:
When a server block occurs, the log file created will highlight which files were being
accessed at the time the block occurred. This needs to be thoroughly checked to ascertain what the problem is. There are many forums that discuss ModSecurity and these are the best place to go to for help working out what the problem might be.
Are you using a good, dedicated FTP program such as FileZilla? Web browser based FTP clients have been known to cause issues with ModSecurity and are not programs we recommend using.
Have you performed a thorough virus scan to ensure you have no vulnerabilities on your PC? You may want to also check all PC’s on your network just in case there is nothing lurking in the background.
Do you have any plugins installed into your web browser that may be trying to scan the server or web pages you are visiting? Browser plugins can be very useful but have often been the cause of ModSecurity issues. An example of this is the Firebug plugin for Firefox which we have found to be the culprit of a number of ModSecurity alerts.
This article may provide some help in reviewing the ModSecurity rules and deciding how to customise the behaviour it’s implementation on your VPS server:
http://success.grownupgeek.com/index.php/2011/01/08/how-troubleshoot-mod_security-rules/

